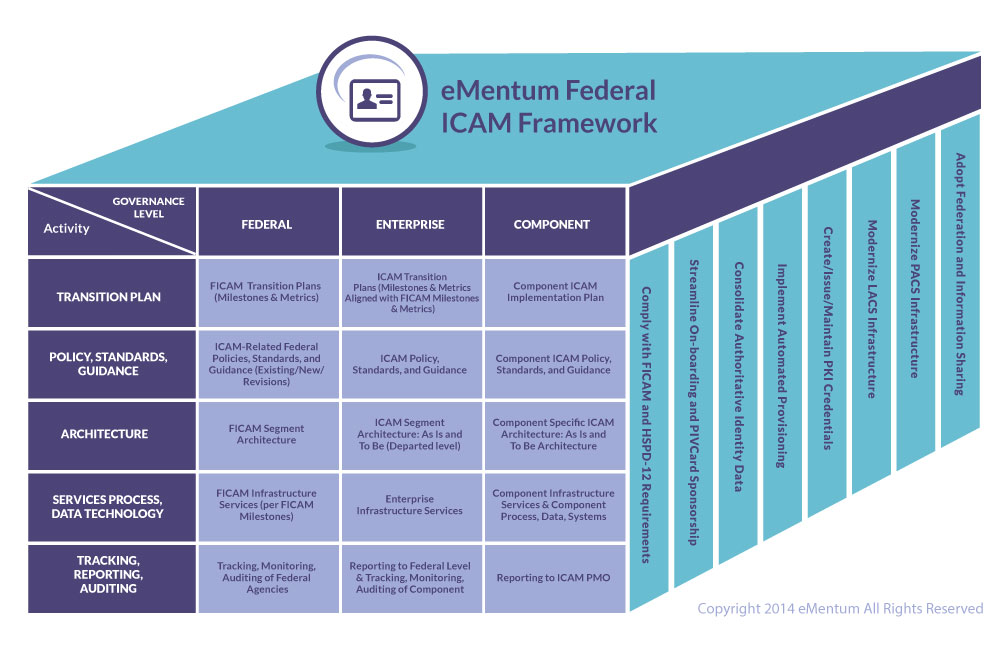
An Introduction to Physical Access Control Systems
Summary: Physical Access Control Systems (PACS) are a key component of the overall security capability of Federal agencies and commercial enterprises as they seek to protect their employees, physical and intellectual property, and other stakeholders’ interests. While these systems have been around for many years, the advent of Homeland Security Presidential Directive 12 (HSPD-12) has created a new focus on standardization of credentials and integration of PACS and their capabilities across the federal space. Click here to view/download white paper.

Implementing Attribute Based Access Control in the Federal Arena
Summary: Recently, the United States Government has shown a considerable interest in Attribute Based Access Control (ABAC) as a means to improve information sharing and IT security. The Federal government is making it a priority to update existing access control infrastructures that use authorization leveraging Role Based Access Control (RBAC) or Identity Based Access Control (IBAC) using Access Control Lists (ACL). Some organizations have even older models such as Discretionary Access Control (DAC) and Mandatory Access Control (MAC). In 2005, Hurricane Katrina (and similar national emergencies since) emphasized the need for multiple Federal, state, and local agencies to share information in a dynamic and flexible manner. The WikiLeaks Incident in 2010 highlighted the government’s needs to further protect and secure its classified materials. The focus on ABAC is a reaction to very real events in our nation that have highlighted the need for a more dynamic, more adaptable logical access control method to protect its resources. Click here to view/download white paper.
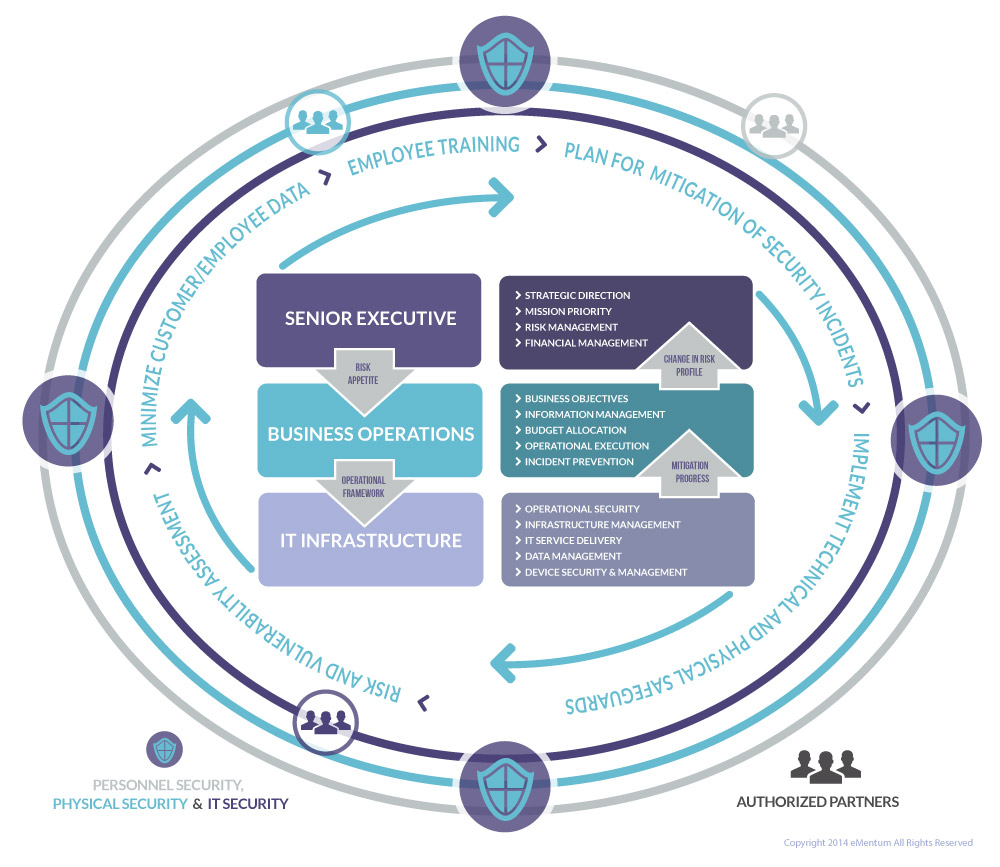
Understanding the Insider Threat
Summary: For decades, the Federal government and US industry focused on external threats, but now that the Internet has connected the world, espionage and theft are largely anonymous and borderless activities. The government and its contractors now look inward and apply new technologies and counterintelligence strategies to detect and deter criminals, spies, or leakers in their midst. Click here to view/download white paper.

Credential Management
Summary: Meeting the challenges of cyber and physical security threats is a necessity for the private and public sectors in the 21st Century. With continually changing threats to security, protecting sensitive data becomes ever more important. It is vitally important for any organization to reliably authenticate an individual’s identity and to limit access to protected resources and information based on that identity Click here to view/download white paper.
Meeting the Portfoliostat Challenge
Summary: Since the turn of the century, the Federal government has increasingly emphasized the need to minimize complexity and redundancy across its information technology investments. Agencies, down to the lowest decision authority, have always tended to act independently, choosing internal implementations and/or custom development before evaluating the suitability of an existing solution, but this has led to a vast proliferation of redundant IT and a contractor community that benefits from sustaining (and growing) this overprovision. The increasing cost of this approach and the increasing number of failed projects has correspondingly increased the spotlight placed on these strategies. Click here to view/download white paper.

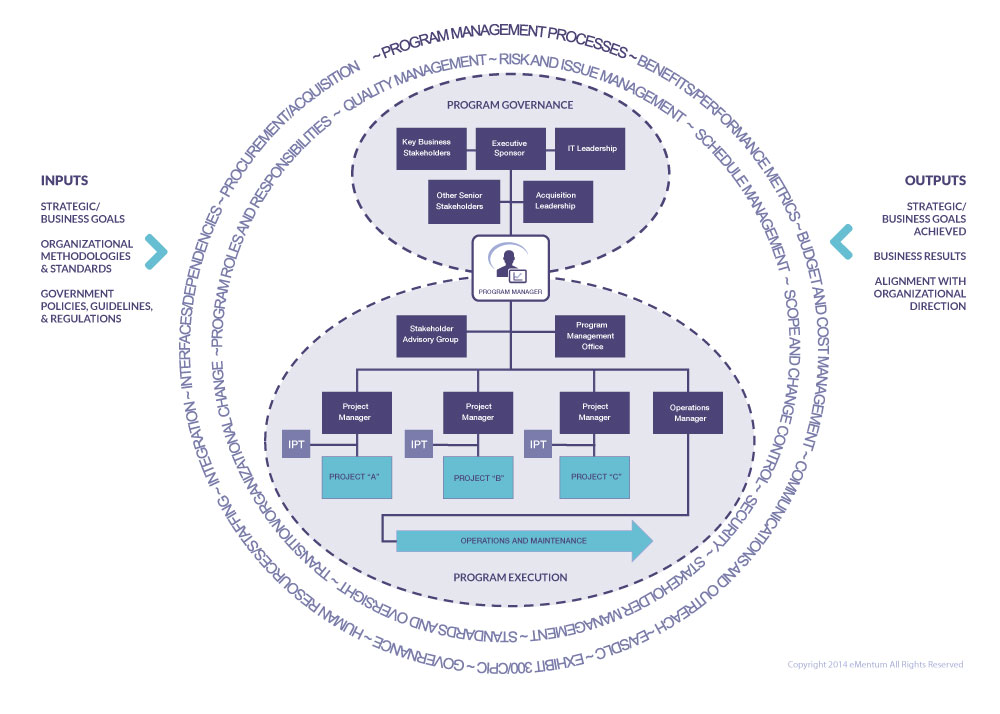
Best Practices In Program Management
Summary: eMentum consultants have been providing program and project management support to the Federal and commercial communities since 1999, and many of our senior leaders have more than twenty-five years of experience in their areas of expertise. This paper is the distillation of that experience into several key points that have helped us maintain happy and successful clients despite highly challenging situations. Click here to view/download white paper.

Why Do I Need A Program Management Office (And How Do I Get One)?
Summary: Due to the often complex and risky nature of projects, many organizations experience pressure for consistency in strategy, communication, responsibilities, and processes as an approach to achieving success without compromising time, scope, cost, and quality.
As Federal budgets continue to tighten, resources become increasingly stretched as their assignments and responsibilities expand. In this environment, where there is a constant pull between strategic objectives and operational issues, it is challenging to maintain balance and focus. Federal programs receive increasingly detailed scrutiny from oversight agencies and from the public, both of whom demand accountability for delivering results in exchange for the very large sums of money committed to them. No project is safe from this scrutiny, no matter how small, as dashboard reporting has become more prevalent for reporting the health of Federal investment portfolios. Click here to view/download white paper.
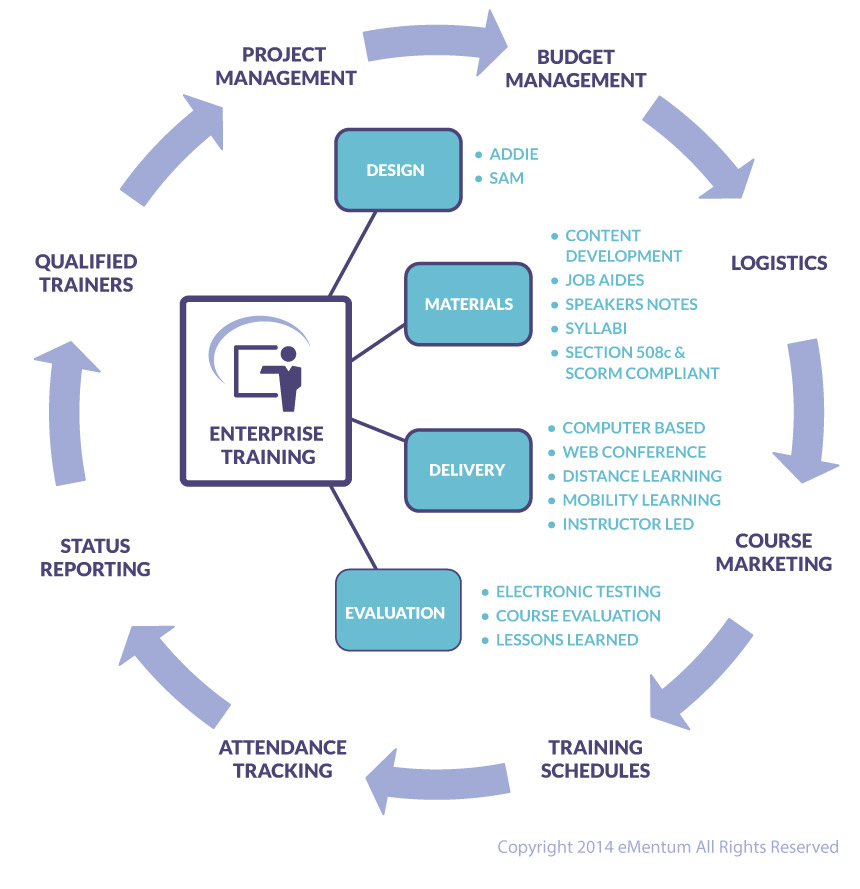
Increasing the Value of Enterprise Training
Summary: Enterprise training in the Government sector has always been a necessary if often overlooked function. Every aspect of an agency has policies, processes, procedures, and systems that need to be deployed to employees, and it can be a challenge to ensure that a common interpretation and a wide-spread distribution of information are achieved. The most efficient way to accomplish this is to hold a formalized training session. Unfortunately, in recent years, training and education has become a lower budgetary priority and is usually one of the first line items to be slashed during fiscal turmoil. When training budgets are cut, necessary, and in some cases mandatory, information may not be conveyed to key personnel in an efficient and timely fashion. Training becomes fragmented and uncoordinated as the enterprise program is downsized and decentralized. Individual programs provide training focused on their individual silos, but may not recognize and account for the interconnectivity between subject areas. As a result, the mission suffers. Click here to view/download white paper.
Innovating IT Solutions through Human Centered Design
Summary: Advances in information technology (IT) are supposed to make life easier for the people who use it, but this isn’t always the case. In too many cases, the human element is ignored when designing an IT solution. The software’s interface is confusing, and users cannot easily find basic, frequently used features. A new system is lightning fast until too many people attempt to log in during normal business hours, and it crashes because capacity planning was ignored. Even worse are situations when an upgrade that was never needed is made to an IT solution that makes things even worse for the end user by removing popular features or implementing enhancements that break core functionality. The result is an end product that disappoints the user community. How could these important factors be overlooked? Click here to view/download white paper.

An Introduction to the Zero Trust Framework
Summary: Despite the increased use of sophisticated data management technologies like firewalls, data encryption, digital identities and strong authentication to help thwart these attacks, data about our institutions and people continues to be compromised. Traditional security controls have not effectively considered users once on the network, or they have been deployed weakly or inconsistently in various stovepipe implementations throughout the enterprise. The rationale is because malicious external actors are presumed kept out and internal users are trusted, but history has shown again and again that not every user, device, or software application that ends up on the network accessing data resources is authorized. This white paper explores the value of an approach known as “Zero Trust” as a potential solution to the ongoing security threat. Click here to view/download white paper.

Public Key Infrastructure (PKI) Basics
Summary: Public Key Infrastructure (PKI) offers great potential for the way forward in information security. Its disciplines and methodologies have permeated a great number of commercial-off-the-shelf (COTS) security products. Protocols are becoming more robust as new and better algorithms are developed and adopted for general use or as key lengths for existing algorithms continue to increase. In the late 1960s, PKI cryptography concepts began to be referenced in classified documents in Great Britain. Prior to this time, PKI was held strictly in the purview of the military, secret services, and intelligence communities. Click here to view/download white paper.

